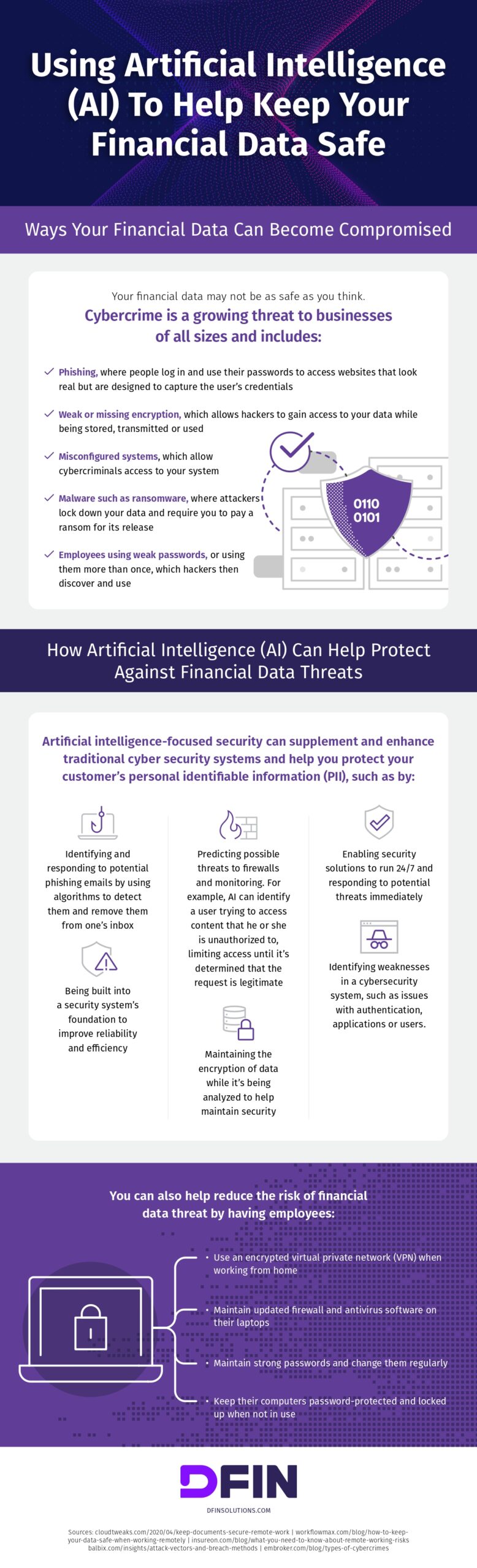
Cybersecurity Tips You Should Follow To Protect Your Business

Getting some cybersecurity tips doesn’t hurt at a time when new technologies are in full swing. Industry 4.0 enjoys the benefits of the Internet of Things, the cloud, artificial intelligence, voice search, chatbots . All of this, however, has increased the risk of cyberattacks.
Businesses targeted by hackers
New technologies have brought about a modernization of businesses that makes their management more straightforward.
However, many entrepreneurs continue without being aware of the security breaches that are being opened. Thus, they expose sensitive data, corporate information, personal issues and business processes.
Hundreds of thousands of euros are in danger due to widespread neglect that cybercriminals do not hesitate to exploit. Charting a cybersecurity tips or strategy is essential to minimize the risks of virtual crime.
Cybersecurity in numbers
A recent study, carried out by the computer security company Mcfee, has analyzed data worldwide. The Economic Impact of Cybercrime-No Slowing Down report shows that in 2017 cybercrime cost more than $ 600,000,000,000.
This figure represents 0.8% of global GDP. Only drug trafficking and corruption exceed this amount.
The study shows that hackers adapt quickly to new technologies. In addition, they take advantage of the sloppiness of employers in terms of digital security.
In 2017, cybercrime cost more than $ 600,000,000,000 USD, 0.8% of global GDP. Only drug trafficking and corruption exceed this amount.
Ransomware is the technique most used by these criminals. It’s about data hijacking. The formula used by the attacker is to introduce a virus into computer equipment and prevent its owners from accessing it. The solution? Pay an amount to the hijacker to regain access.
However, the technology to combat this scourge exists and is available. Now companies must be aware of this cybersecurity tips and implement security measures.
Why do we need elements of business digital security
The answer is obvious, even if so little action is taken:
- A company needs the data collected through digital devices to be effectively protected.
- Personal data of workers and customers must remain anonymous, which is also a way to fight against phishing.
- Corporate information and processes developed by companies must be kept safe in all business departments.
Measures against corporate cyberattacks
The only way to fight against cybercrime is to catch up in this field and take the necessary measures to protect the company. It is a solution that must be constant.
The world of cybercrime is advancing even faster than new technologies. This is why monitoring the computer security of a company must be a continuous methodology that adapts to unknown dangers.
It would be convenient for companies to start implementing a department dedicated exclusively to this issue. Employees assigned to this task should be trained on the need for awareness in this field and what actions need to be taken to counter different attacks.
Data storage
Many entrepreneurs don’t even know where they keep their business data. They may even be using various media: mobile devices, local drives, the cloud, disk-based systems, and more.
Each type of support must have its security solution. Apart from this, the most consistent thing is to say goodbye to layered security and adopt an integrated system.
Access limit
Managers and team leaders must develop a data access list based on the needs of each employee. Only workers who need this information should be authorized.
In addition, a system that records access is much more reliable. In this way, the employee who accesses the information will be identified ipso facto.
Next-generation device protection
The BYOD policy, which allows employees to work with their mobile device, has become fashionable. This means that the worker uses his smartphone or tablet to work and for personal use. This dramatically increases the risks.
An integrated state-of-the-art device protection system should be activated. The formula allows devices to communicate with each other, but it also allows us to isolate those suspected of being attacked. Endpoints will be essential in this task.
Risk study
It is impossible to implement a preventive system that works 100%. It would be too expensive and unrealistic. It is best to conduct a risk study that identifies the most critical and most vulnerable systems.
In this sense, you have to be aware that the ways of attacking are constantly changing. It is crucial to equip yourself with tools dedicated to tracking in real-time and that act to eliminate the threat.
Automate processes
“Infographic created by DFIN, a data room provider”
It is useless that time, money and resources are wasted in simple processes that can be automated. With this measure, the entire infrastructure can be dedicated to the most delicate and sensitive issues.
Periodic backups
This option is essential. Regular backups provide backups that can save a company’s life in the event of security breaches. A daily backup is an excellent way to keep your peace of mind.
Restoration points
All computers must have their restore point. In addition to this, you have to make sure that they work correctly. If necessary, we can return the functionality to the device, returning it to a time before the problem appeared.
As can be seen, in terms of safety, all precautions are little. Companies must do everything they can to implement an exemplary system according to their needs and their data volume.
Having a company or personnel specialized in this field will help to increase the level of efficiency. A sound security system should not be seen as an expense but as an investment that can save the entrepreneur many headaches and money. Regardless, it’s a good idea to take advantage of these cybersecurity tips.